Popcustoms.com
Strait petrochemical building 801 #, Jinjiang ,
Quanzhou city, Fujian province, China
Last Updated: Feb 01, 2021
Thank you for using POPCUSTOMS! Before using or accessing our platform, please read this Terms of Service (the “Terms of Service”) carefully. This document is a legally binding contract between POPCUSTOMS and you, the User (as defined below), for the use of the applications, software, products and services provided by POPCUSTOMS (collectively, the “Service”) and as such, we have tried to make it as clear as possible. In addition to the full legal terms and text, we have provided short non-binding summaries with each clause. These summaries do not aim to replace or misrepresent the full text.
A. Definitions
Summary: These terms are used throughout this Terms of Service and it’s important that you understand what we are referring to when we use them.
Terms not defined in this section shall have the meaning provided elsewhere in the Terms of Service.
“Agreement” refers, collectively, to all the terms, conditions, notices contained or referenced in this document (the “Terms of Service,”) and all other operating rules, policies, including POPCUSTOMS Privacy Policy and POPCUSTOMS Intellectual Property Policy, and procedures that we may publish from time to time on the Website including but not limited to Shipping, Payments, and Returns.
“Content” refers to content featured or displayed through the Website, including without limitation text, data, articles, images, photographs, graphics, software, applications, designs, features, and other materials that are available on the Website or otherwise available through the Service.
“Customers” refers to individuals or entities that purchase Your Products through a Sales Channel.
“Orders” refers to Your Products once they have been purchased by You or Your customers.
“Produced Orders” refers to Orders that have been completed and shipped.
“Products” refers to all products offered by different Providers on our Website including, but not limited to clothing, accessories, home decor, kitchenware, footwear and stationary.
“Factories” refers to the organizations and companies that POPCUSTOMS partners with in the scope of its Service to offer Products to You.
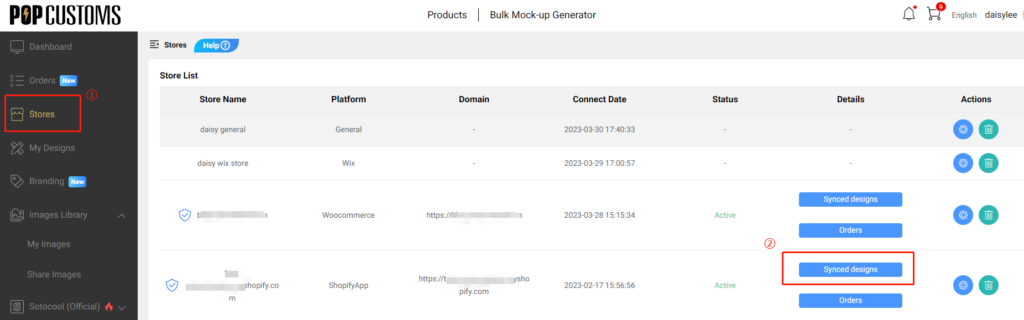
“Stores” refers to the other websites and platforms that You use to sell Your Products, including but not limited to Shopify, Woocommerce, Ebay, or Etsy, etc.
“Us” and “We” refers to POPCUSTOMS, Inc., as well as our affiliates, directors, subsidiaries, contractors, licensors, officers, agents, and employees.
“User,” “You,” “Your” refers to the individual person, company, or organization that has visited or is using the Website or Service; that accesses or uses any part of the account; or that directs the use of the account in the performance of its functions.
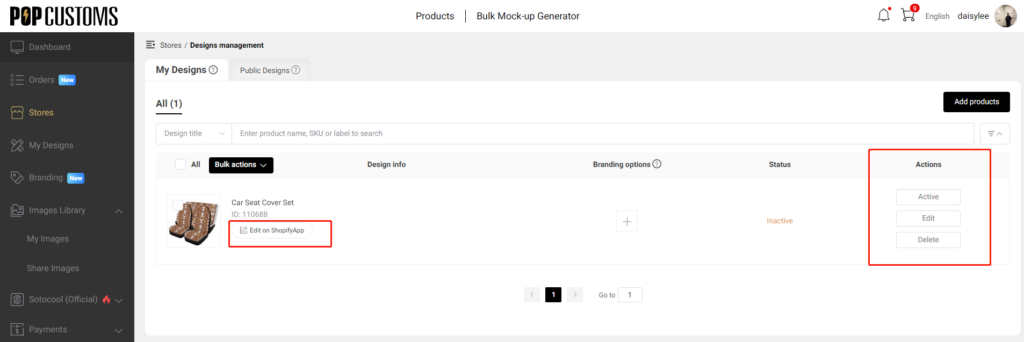
“Products” refers to Products created by Users adding Content using the Service.
“Mockups” or “Templates” are visual representations of Users’ Products created through the Service.
“User-Generated Content” is Content, written or otherwise that is created or uploaded by our Users.
“Website” refers to POPCUSTOMS’s website located at Popcustoms.com, and all content, services and products provided by POPCUSTOMS through the Website. It also includes POPCUSTOMS-owned subdomains of Popcustoms.com, such as app.Popcustoms.com, POPCUSTOMSapp.com and all subdomains of POPCUSTOMSapp.com such as app.POPCUSTOMSapp.com, and the use of future and current POPCUSTOMS plugins, such as those available in the Shopify App store, Woocommerce, Etsy,. Occasionally, POPCUSTOMS plugin pages and websites owned by POPCUSTOMS may provide additional or different terms of service. If those additional terms conflict with these Terms of Service, the terms in the additional terms with regard to the matter in conflict shall apply.
“Your Content” is Content that you create or own.
B. General
When You use Our Services and Content, You are agreeing to:
Our Terms of Service
Our Privacy Policy
Our Copyright Policy
Any other terms or policies we reference below.
Except as they may be supplemented by additional terms and conditions, policies, guidelines or standards, the Agreement constitutes the entire understanding between POPCUSTOMS and You pertaining to the subject matter hereof, and supersedes any and all prior oral or written understandings or agreements between POPCUSTOMS and You in relation to the access to and use of the Service.
If any provision of these Terms of Service are held to be invalid or unenforceable, such provision will be struck and will not affect the validity and enforceability of the remaining provisions.
Questions about the Terms of Service? Contact us.
C. When Do These Terms Apply?
Summary: By using POPCUSTOMS, you are agreeing to all the terms below.
By using the Service, You acknowledge that You accept and agree to be bound by these Terms of Service. If You do not agree to these Terms of Service, You may not access the Service, and if You are already registered, cancel Your account.
D. Can These Terms Be Modified?
Summary: We can change these Terms of Service, and if the changes are big, we’ll let you know.
POPCUSTOMS reserves the right to revise the Terms of Service from time to time and the most current version will always be posted on our Website. If a revision, in our sole discretion, is material we will notify You. The “Last Updated” date at the top of the Terms of Service reflects the date of the last modification. Your use of the Service following the effective date of any modifications to the Terms of Service will constitute your acceptance of such modification. If You do not agree to the new Terms of Service, You should stop using the Service and cancel Your account.
E. What Is the Scope of POPCUSTOMS‘s Services?
Summary: POPCUSTOMS is an online platform that allows you to create and connect your store to sell products with your content by working with various Print on Demand Providers from around the world. You focus on creating and selling, we handle the rest.
POPCUSTOMS is an online marketplace for print on demand/embroider on demand dropshipping and public designs on demand . We partner with various Providers to offer You Products that You can customize with Your Content and sell to Customers. We also maintain and create integrations with different Sales Channels so that Your Products can be easily published to your Stores. When Your Products are purchased by Customers through a Sales Channel, We are notified and We start working with factories print and deliver Your Products to the Customers.
Summary: POPCUSTOMS is not only a platform, we are also a factory supply chain to sell products with high quality and best prices .
POPCUSTOMS has control over and does guarantee the final quality of Your Product. And we make any promises that Your Product will look like Your Mockup.
Due to the nature of the Internet, POPCUSTOMS cannot guarantee uninterrupted access and availability of the POPCUSTOMS Service. We reserve the right to restrict the availability of our Service or certain features if necessary in view of capacity limits or the integrity of our servers. We also reserve the right to restrict access when performing maintenance measures to ensure the proper working and functioning of the POPCUSTOMS Service. POPCUSTOMS can improve or modify its Service and may introduce new offerings from time to time.
Summary: POPCUSTOMS guarantee that our website will be online 100% of the time.Just due to the nature of product development and the Internet, our website may have periodic downtimes.
F. Who Can Access POPCUSTOMS and Use the Service?
Summary: You have to be at least 18 years old to use our service and if you are signing up on behalf of someone else, you are acknowledging that you have the right to do so. Certain features of our platform may have additional terms other than those here.
You must be at least 18 years old and able to access and use the Service or to create a POPCUSTOMS account. By accessing and using our Service, you represent and warrant that you are 18 years of age or older and have the legal capacity and authority to enter into a contract.
If you open an account on behalf of a company, organization, or other entity, then “You” includes you and that entity, and You represent and warrant that You are authorized to grant all permissions and licenses provided in this Terms of Service and bind the entity to these Terms of Service, and that you agree to these Terms of Service on the entity’s behalf.
The access to or use of certain areas and features of the Service may be subject to separate policies, standards or guidelines, or may require that you accept additional terms and conditions. If there is a conflict between these Terms of Service and the terms and conditions applicable to a specific area or feature of the POPCUSTOMS Service, the more specific terms and conditions will apply, unless specified otherwise.
To use our Service, You have to register an account. Details on how to do so are provided in the next section.
You understand and agree that You are responsible for paying any and all applicable taxes that may be due as a result of your use of the Service.
G. What Are the Rules for Creating and Maintaining an Account?
Summary: We have certain requirements that you must abide by when you create an account with Us.
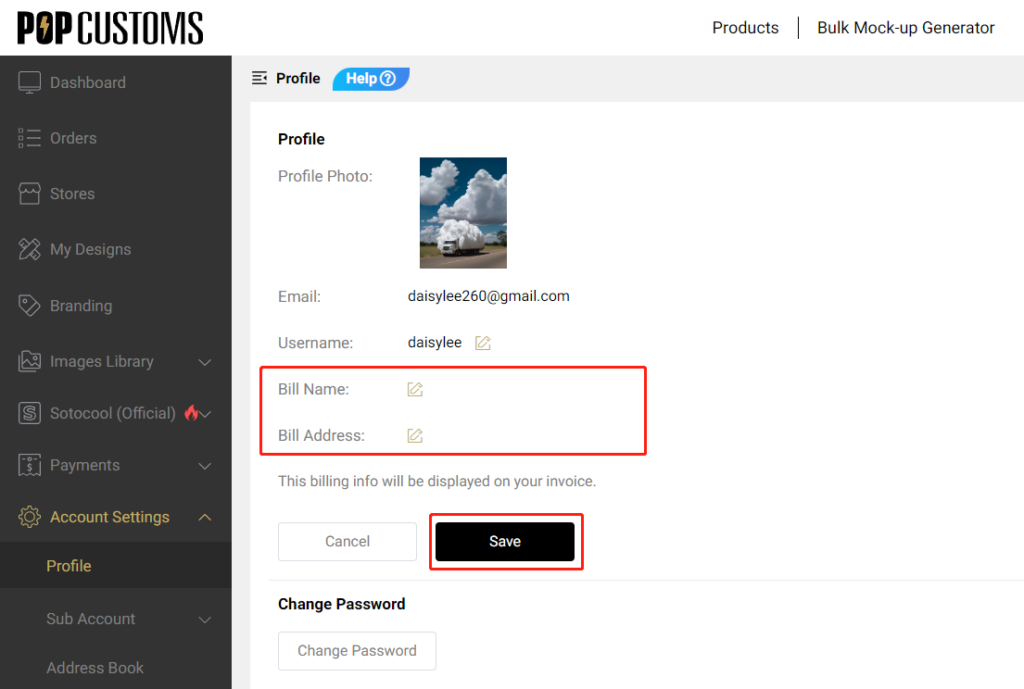
To create a POPCUSTOMS Account You may be required to provide POPCUSTOMS with certain personal information, which may include your full legal name, current address, phone number, email address, and payment information. This information will be held and used in accordance with POPCUSTOMS’s Privacy Policy. You agree that You will supply accurate and complete information to POPCUSTOMS, and that You will update that information promptly after it changes. You further agree that:
You shall not create an account or access the Service if You are under the age of 18;
You shall not have more than one account at any given time, and shall not create an account using a false identity or information, or on behalf of someone other than yourself or your entity, which has provided you authorization to create the account on behalf of it;
You shall not have an account or use the Service if You have been previously removed by the Company;
We may reject your registration or cancel an existing registration for any reason at our sole discretion;
We will use the email address you provide as the primary method of communication.
Any harassment or insult towards POPCUSTOMS employees may result in immediate account termination.
You are solely responsible for keeping your account credentials secure and you may not disclose your credentials to any third party. You must immediately notify POPCUSTOMS if you have any reason to suspect that your credentials have been compromised, lost or stolen or in the case of any actual or suspected unauthorized use of your POPCUSTOMS Account. You are solely responsible for any and all activities performed through your POPCUSTOMS account. POPCUSTOMS will not be liable for any loss that You may incur as a result of someone else using Your username or password, either with or without Your knowledge. To the extent allowable by law, you shall be liable for any expenses and reasonable attorney’s fees for your failure to safeguard user and password information and/or promptly notify the Company about unauthorized use of your account or breach of your account information or password.
POPCUSTOMS expressly disclaims any and all liability arising from revocation, cancellation, or suspension of your account for any reason. Your account and registration will terminate immediately upon your breach of any of the terms herein. You may terminate your account and participation as a registered user at any time from your Account Settings > Personal Data > Delete my data. Before proceeding with deleting your account, make sure that you have disconnected your store from the respective sales channels, unsubscribed from the business plan and removed your registered credit card. Deleting your account is irreversible and you will not be able to access the data afterwards. Nonetheless, you will still be responsible for any and all pending orders and charges.
H. What Are Your Rights to Content on POPCUSTOMS?
Summary: All content you upload is owned by you. If we are notified or if we believe that the content is not yours, or if the content doesn’t meet our standards, we will remove it at our discretion. By uploading content to POPCUSTOMS, you allow us to use your content for things like marketing and education of POPCUSTOMS users.
POPCUSTOMS grants You a limited, revocable, non-exclusive, non-transferable license to access and use the Service for Your own individual use subject to the other terms of this Terms of Service. All rights, title, and interest in and to the Service not expressly granted herein are reserved by the Company.
POPCUSTOMS allows You to upload and post Content to our Website. Anything that You put on the Products remains Your Content. You retain all rights in, other than the rights expressly granted to POPCUSTOMS below and any that you may grant to your Customers, and are solely responsible for Your Content.
You can only post Content that is either Yours, or for which you have written authorization from the Content owner. You represent and warrant that any Content you post is owned by You or that You have authorization from the Content owner to post it. More detailed information can be found in the POPCUSTOMS Intellectual Property Policy. By posting Content, You accept those terms as well. If You believe that someone has improperly used Your copyrights or trademarks, please report it to us as set forth in the Intellectual Property Policy.
By using the POPCUSTOMS Service, You grant POPCUSTOMS a non-exclusive, transferable, sublicensable, royalty-free, and worldwide license to use, store, display, reproduce, save, modify, create derivative works, perform and distribute Your Content solely for the purpose of operating, developing, and promoting the PopCustoms Service.
As a condition of use of the Service, You agree not to use the Service for any purpose that is prohibited by these Terms of Service. You are responsible for all of your activity in connection with the Service and you shall abide by all local, state, national, and international laws and regulations and any applicable regulatory codes. You agree to the following:
You may not resell, rent, lease, loan, sublicense, distribute, or otherwise transfer rights to the Service.
You may not modify, reverse engineer, decompile or disassemble the Service.
You may not copy, adapt, alter, modify, translate, or create derivative works of the Service without written authorization of POPCUSTOMS.
You may not permit other individuals to use the Service, including but not limited to shared use via a network connection, except under these Terms of Service.
You may not circumvent or disable any technological features or measures in the services that are designed for protection of intellectual property rights.
You may not use the Service in an attempt to, or in conjunction with, any device, program, or service designed to circumvent technological measures employed to control access to, or the rights in, a content file or other work protected by the copyright laws of any jurisdiction.
You may not use or access the Service to compile data in a manner that is used or usable by a competitive product or service.
You shall not use your Account to advertise, solicit, or transmit any commercial advertisements, including chain letters, junk e-mail or repetitive messages to anyone.
You shall not use your Account to engage in any illegal conduct.
You shall monitor your Account to restrict use by minors, and You will deny access to children under the age of 13. You accept full responsibility for any unauthorized use of the Service by minors in connection with your Account and You are responsible for any use of your credit card or other payment instrument by minors.
You shall not use the Service to order and resell blank Products without customizing them with your artwork.
Any such forbidden use shall immediately terminate Your license to the Service.
POPCUSTOMS may use its discretion to remove Your Content from our Service, at any time, with or without prior notice to you, if it violates any of our Terms of Service or policies or is reported to be infringing on intellectual property rights of others. POPCUSTOMS is not obligated to monitor or police Your Content. In addition to intellectual property concerns, Content that contains any of the below is prohibited and may also lead to termination of Your account.
Child Exploitation: You may not post or upload Content that exploits or abuses children, including but not limited to images or depictions of child abuse or sexual abuse, or that presents children in a sexual manner.
Harassment, Bullying, Defamation and Threats: You may not post or upload Content that harasses, bullies, defames or threatens a specific individual.
Hateful Content: You may not post or upload Content that condones or promotes violence against people based on race, ethnicity, color, national origin, religion, age, gender, sexual orientation, disability, medical condition or veteran status.
Illegal Activities: You may not post or upload Content that facilitates or promotes activities that go against the laws of the jurisdictions in which you operate or do business.
Intellectual Property: You may not post or upload Content that infringes on the copyright or trademarks of others.
Personal and Confidential Information: You may not post or upload any Content that contains personally identifiable information sensitive personal information, or confidential information, such as credit card numbers, confidential national ID numbers, or account passwords unless you have consent from the person to whom the information belongs or who is otherwise authorized to provide such consent.
Self-Harm: You may not post or upload Content that promotes self-harm.
Terrorist Organizations: You may not post or upload Content that implies or promotes support or funding of, or membership in, a terrorist organization.
When You use the Service, POPCUSTOMS reserves the right to view, monitor, and record activity without notice or further permission from You, to the fullest extent permitted by applicable law, although we have no obligation to do so. Any information obtained by monitoring, reviewing, or recording is subject to review by law enforcement organizations in connection with the investigation or prosecution of possible criminal activity involving use of the Service.
I. How Do Payments Work on POPCUSTOMS?
Summary: POPCUSTOMS will only charge you fees if you subscribe to a POPCUSTOMS Membership Premium Plan. No products are produced or shipped unless payment for those products has first been received via credit/debit, or from an existing POPCUSTOMS balance. Users have the option to change settings for when and how often they are charged. You cannot withdraw “points” or “coupons” or ” discounts”.
Unless Users subscribe to the POPCUSTOMS Membership Premium Plan, there are no fees or charges for the platform itself.
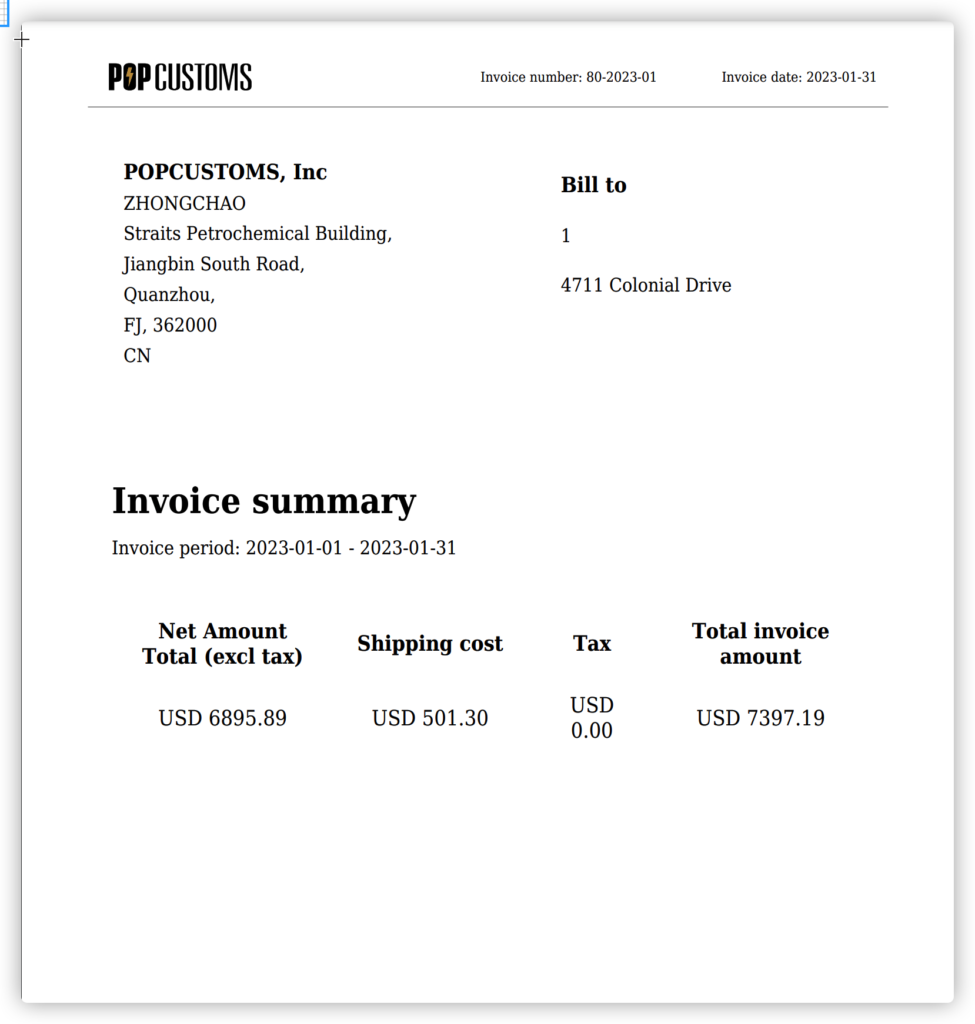
To order samples of Your Products or to fulfill any Customer Orders, You must pay for the Order in advance. The price You pay will be the price of the Product plus shipping and taxes (if applicable). These prices can be found in the POPCUSTOMS Catalog and on our Shipping Rates page. Orders will not be processed until payment has been received by POPCUSTOMS.
POPCUSTOMS cannot pull funds that You may have available in any Sales Channel. In order to process payments on POPCUSTOMS, You need to either have a Credit or Debit card on file or connect POPCUSTOMS to your PayPal/Payoneer/ Bank account. By default, POPCUSTOMS will charge funds for Orders from an existing POPCUSTOMS balance first, and if there is a remaining balance due then POPCUSTOMS will charge any saved Credit or Debit cards.
POPCUSTOMS charges Users when Orders are sent to production. Users have the option to change their settings to adjust how often Orders are sent to production and whether POPCUSTOMS charges per Order or for multiple Orders together. These settings can be found here, after You create an account and connect a Sales Channel.
POPCUSTOMS may issue a coupon. A coupon is virtual money that can be used for paying for manual and sample orders. You may use a coupon only for a single order. Multiple coupons cannot be combined. Each coupon’s value is divided according to the total line items in the order. It cannot be converted to cash or withdrawn.
If you have an issue with your order, contact POPCUSTOMS before disputing your claim with your credit card company. If you have filed a dispute with your credit card company, we will not be able to issue you a refund as well, and we cannot make any refunds or replacements until the dispute is resolved or cancelled. If there are Order issues and after an investigation POPCUSTOMS offers you a refund, this will be provided in the form of a POPCUSTOMS credit and will appear in your POPCUSTOMS balance.
Once a user withdraws funds from POPCUSTOMS balance it will be sent to the same payment source where it initially came from, whether it is a credit/debit card or a PayPal account. If a top-up is made via PayPal, withdrawal can only be made to the same PayPal account. In case the initial payment was made with a card, the POPCUSTOMS balance withdrawal will take place in the form of a credit/debit card full or partial refund. Subscription bonus provided to subscribers of the POPCUSTOMS Premium Plan will not be able to be withdrawn.
Users are responsible for paying any necessary sales tax on their transactions. Because of the nature of dropshipping businesses, taxes differ depending on who produces or sells the Product, and where it is delivered. POPCUSTOMS recommends that You consult with an outside tax accountant.
European Union (EU) regulations require POPCUSTOMS to collect Value Added Tax (“VAT”) on all orders produced and shipped within the EU. Users with businesses registered with the EU may apply for a VAT Exemption if the Users have a valid VAT number. If you qualify for a VAT exemption, contact POPCUSTOMS Merchant Support with your VAT number and business details and we will apply the exemption in our system.
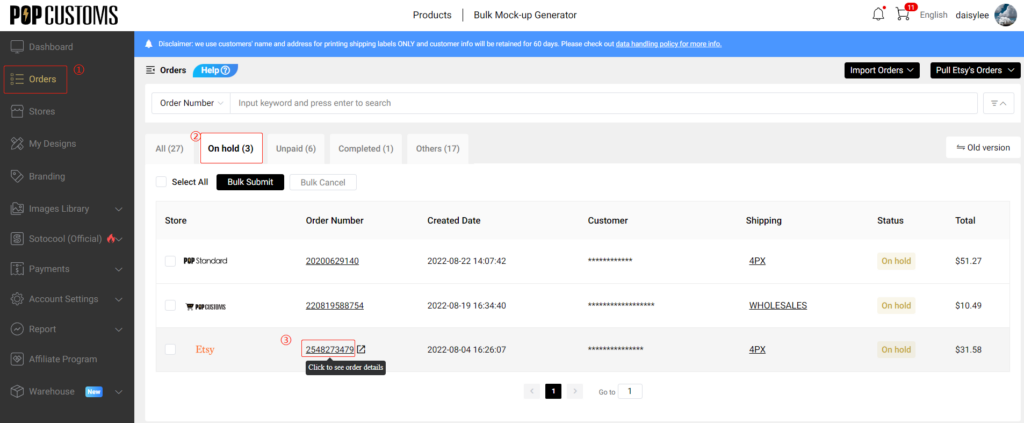
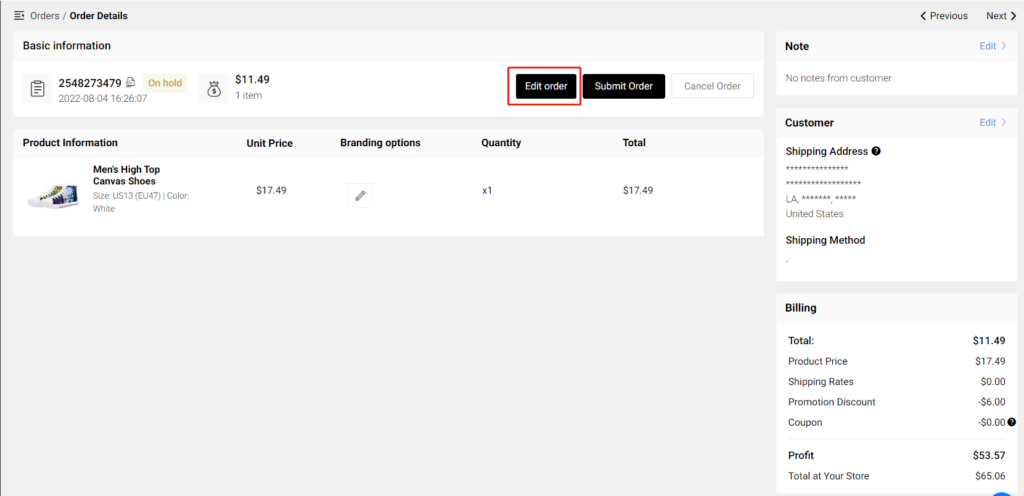
J. How Does POPCUSTOMS Handle Order Related Issues?
Summary: If you have an issue with your order, contact POPCUSTOMS directly within 30 days of product delivery and provide a detailed description of your issue, accompanied by relevant photo or video evidence that support your case. After investigation, we will determine if you are eligible to receive a replacement at no cost to you. Some issues do not qualify for replacement, they are outlined below.
More : https://Popcustoms.com/return-and-refund-policy/1527517
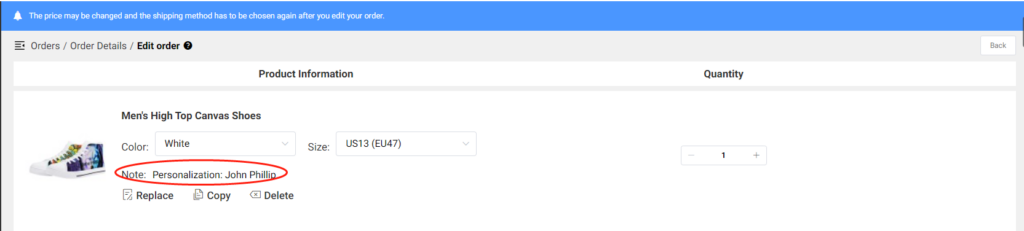
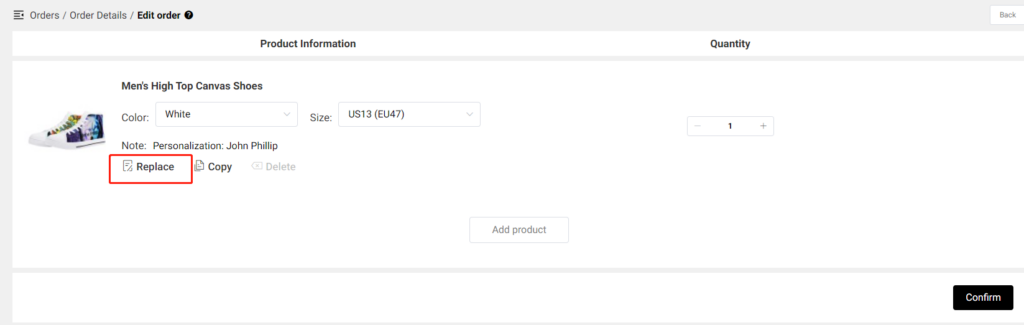
K. Embroidery
Summary: Embroidery is not like other print on demand methods and to avoid issues and complications, you must follow our embroidery guide closely.
All designs for embroidery products must conform to the guidelines found in our Embroidery Design Guide.
Images that do not meet guidelines, may be edited by our Print Partners during the digitization process to become eligible for embroidery. The final embroidered image may differ from your submitted artwork. In these situations, you are not eligible for replacements or refunds for those items.
All images submitted for embroidery for the first time will have a 24-48hour digitization period. If there are multiple items in that order, the whole order will be delayed.
More : https://Popcustoms.com/introduction/print-on-demand?section=eod
L. Can You Use POPCUSTOMS‘s Image and Name?
Summary: We take intellectual property rights seriously and we kindly ask you to respect ours.
POPCUSTOMS, Popcustoms.com, POPCUSTOMSsapp.com, and other POPCUSTOMS graphics, logos, designs, page headers, button icons, scripts and service names are registered trademarks, or trade dress of POPCUSTOMS that may not be used in connection with any Product or service without the prior written consent of POPCUSTOMS. The images and icons available in our brand and press kit may be used by partners and third party sites as long as the appropriate links to the POPCUSTOMS Website are included. POPCUSTOMS reserves the right to request removal of Your use of the images and icons at any time.
M. Limitation of Liability
Summary: We are not responsible for any losses you incur as a result of using our service. We are not responsible if you break the law or breach this agreement and are sued as a result. Please read this section carefully; it limits our obligation and responsibilities to you.
Limitation of Liability. IN NO EVENT SHALL POPCUSTOMS, ITS OFFICER, DIRECTORS, AGENTS, AFFILIATES, EMPLOYEES, ADVERTISES, OR PROVIDERS BE LIABLE FOR ANY INDIRECT, INCIDENTAL, CONSEQUENTIAL OR PUNITIVE DAMAGES INCLUDING, BUT NOT LIMITED TO, LOSS OF USE, LOSS OF PROFITS, OR LOSS OF DATA, WHETHER IN AN ACTION IN CONTRACT, TORT (INCLUDING BUT NOT LIMITED TO NEGLIGENCE), EQUITY OR OTHERWISE, OR FOR DAMAGES IN THE AGGREGATE EXCEEDING THE AMOUNT OF THE FEES PAID AND PAYABLE BY YOU TO PopCustoms OR $100.00 (WHICHEVER IS MORE), ARISING OUT OF OR IN ANY WAY CONNECTED WITH THE USE OF THIS SERVICE. SOME JURISDICTIONS DO NOT ALLOW THE EXCLUSION OR LIMITATION OF LIABILITY, SO THE ABOVE LIMITATIONS MAY NOT APPLY TO YOU.
N. What if I Have Legal Issues with POPCUSTOMS?
Summary: If you have legal issues with POPCUSTOMS, you agree to talk to us first, and if we can’t resolve the situation together, we will follow professional procedures for arbitration. If the issue isn’t arbitrable, all legal issues will be handled in the State of Delaware.
If a dispute arises from or relates to these Terms of Service, You agree to first contact POPCUSTOMS Merchant Support to attempt to resolve the issue. If the dispute cannot be settled through direct discussions, the parties agree to endeavor first to settle the dispute by mediation administered by the American Arbitration Association under its Commercial Mediation Procedures before resorting to arbitration. The parties further agree that any unresolved controversy or claim arising out of or relating to the Terms of Service shall be settled by arbitration administered by the American Arbitration Association in accordance with its Commercial Arbitration Rules and judgment on the award rendered by the arbitrator(s) may be entered in any court having jurisdiction thereof.
To the extent any claim, dispute or controversy regarding POPCUSTOMS or our Service isn’t arbitrable under applicable laws or otherwise, You and POPCUSTOMS both agree that any claim or dispute regarding POPCUSTOMS will be resolved exclusively in accordance with Clause N.3 of these Terms of Service.
These Terms of Service shall be governed by the laws of the Country of USA/ CN, without respect to its conflict of laws principles. You agree to submit to the personal jurisdiction of the United States District Court.
O. POPCUSTOMS Membership Premium Plan
Summary: POPCUSTOMS has a yearly subscription plan that offers upgraded functions and services and discounts on all products. If you block the account and will stop the plan. And if you want to out you have to cancel, before the renewal date.
Recurring Subscription
By subscribing to the POPCUSTOMS Premium Plan, you will receive discounts of up to 20% on all POPCUSTOMS products and the subscription will continue month-to-month or year-to-year until cancellation or termination. You must cancel your subscription before it renews each month/year in order to avoid billing for the next subscription period.
Billing
By starting your subscription, you authorize us to charge you a full subscription fee. You authorize us to charge your payment card for these amounts.
POPCUSTOMS reserves the right to adjust pricing for our service or any components thereof in any manner and at any time as we may determine in sole and absolute discretion. Any price changes to your service will take effect following a notice by email to you.
You will be charged for the subscription fee immediately and the charges will auto-renew every month for every year for yearly subscriptions unless you cancel the subscription.
We automatically charge your payment card every month or every year on the calendar day corresponding to the commencement of your subscription.
Cancellation
SUBSCRIPTION FEE CHARGES ARE NON-REFUNDABLE AND THERE ARE NO REFUNDS OR CREDIT FOR PARTIALLY USED SUBSCRIPTION PERIODS. After a cancellation, you will continue to have access to the discounts throughout the end of your billing cycle.